TLS Handshaking
Introduction
This page is just to remind me how this works
TLS Handshake and Ephemeral Keys
Overview
Transport Layer Security (TLS) is the protocol that secures communication between a client and a server. It provides encryption, authentication, and integrity. The handshake process establishes a shared session key used for encrypting all subsequent traffic.
TLS Handshake (TLS 1.3)
- Client Hello: The client initiates the handshake, sending supported TLS versions, cipher suites, and a random value.
- Server Hello + Certificate: The server chooses a cipher suite, sends its certificate (public key + identity), and its own random value.
- Ephemeral Key Exchange (ECDHE): Client and server exchange ephemeral public keys. Each side uses its private ephemeral key and the other’s public ephemeral key to compute the same shared secret.
- Session Key Derivation: Both sides derive a symmetric session key from the shared secret and random values. This key is never sent over the network.
- Secure Communication: All application data is encrypted with the symmetric session key. Only the client and server can decrypt it.
Ephemeral Keys
- Definition: Ephemeral means temporary, single-use keys created only for the duration of one TLS session.
- Purpose: They provide forward secrecy. Even if a server’s long-term private key is stolen later, past traffic cannot be decrypted.
- Lifecycle: Generated at the start of the handshake, used to derive the session key, and then discarded.
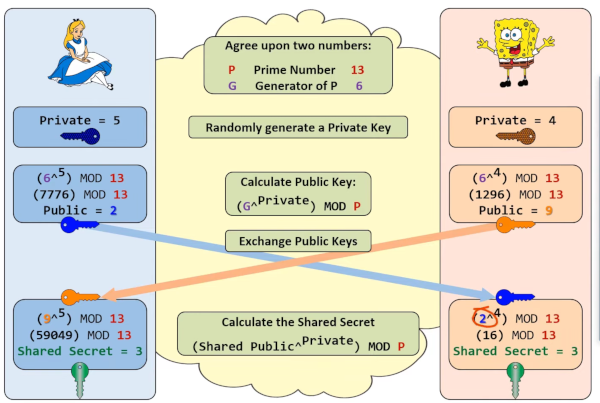
Diffie-Hellman Key Exchange
- Goal: Allow two parties to compute the same shared secret without sending the secret itself over the network.
- Process:
- Each side generates a private ephemeral key.
- Each side computes a public ephemeral key from its private key.
- They exchange public ephemeral keys.
- Each side combines its private key with the other’s public key to compute the same shared secret.
- Security: An eavesdropper cannot compute the shared secret without knowing one of the private ephemeral keys.
So to put it into English, the maths dictates when one side shares a public value and combines it with their public value and private value the number will be the same.
Elliptic Curve Diffie-Hellman (ECDHE)
- ECDHE is a modern variant of Diffie-Hellman that uses elliptic curves.
- Advantages:
- Stronger security per bit compared to classic DH.
- Faster computations, making it efficient for TLS 1.3.
- Usage: TLS 1.3 almost always uses ECDHE for its key exchange.
Session Key
- Derived from the shared secret and random values exchanged during the handshake.
- Used for symmetric encryption (e.g., AES, ChaCha20).
- Never transmitted; both client and server compute it independently.
- Ensures that only the client and server can encrypt and decrypt the traffic.
Identity Verification
- The server’s certificate allows the client to confirm the server’s identity.
- With SslMode=VerifyFull (in Npgsql), the client checks:
- The certificate is signed by a trusted CA (RootCertificate).
- The hostname matches the certificate’s Subject Alternative Name (SAN).
- If verification fails, the connection is refused.